Customer data now sits at the center of modern engagement. It powers acquisition, onboarding, AI-driven personalization, retention, and real-time messaging. That same data also brings responsibility. As its use expands across teams and channels, so does accountability for how it is collected, accessed, and activated.
According to a recent report, the global average cost of a data breach stands at USD 4.4 million. For marketing teams, this is not an abstract security statistic. Decisions about data ingestion, storage, access, and activation are now part of everyday marketing operations.
Customer engagement platforms sit at the heart of this shift. They are where customer data is collected from devices and backend systems, combined with historical context, and activated across journeys, campaigns, and channels. As a result, data security needs to be evaluated across the full lifecycle of data, not at a single point.
The sections that follow examine how customer data is secured within CleverTap through this lifecycle lens:
- How customer data is ingested securely from devices, backend systems, and bulk imports.
- How data is protected while it is stored and processed inside the platform.
- How access is controlled when teams work with that data day to day.
- How data is secured as it moves out for activation, including advanced controls such as key ownership and tokenization for organizations with stricter requirements.
How customer data securely enters the CleverTap platform
Customer data enters a customer engagement platform through multiple paths, each with a different risk profile. Some data is generated in real time from customer interactions on apps or websites. Other data is pushed from backend systems or uploaded in bulk from company servers.
Common ingestion paths include CleverTap Software Development Kits (SDKs) embedded in mobile apps and websites, Application Programming Interfaces (APIs) used by backend systems such as CRMs or billing platforms, and file imports used for historical or large scale datasets from company servers.
Regardless of the source, the goal at this stage is the same: ensure data arrives intact, protected from interception, and accepted only from approved systems.
For real-time collection through SDKs, the primary risk lies in transmission over public networks. Data is generated on devices that are outside the control of both the client and the CleverTap platform and sent continuously over the internet. In addition to transport level protection using HTTPS with Transport Layer Security version 1.2 (TLS 1.2), sensitive SDK data in transit is encrypted using Advanced Encryption Standard (AES 256), which is the industry standard for encryption today. This ensures intercepted data remains unreadable until it reaches the platform.
Encryption is the process of protecting data by converting it from a readable form into an unreadable one using a defined algorithm and a key. Its purpose is to ensure that even if data is accessed, copied, or intercepted, it cannot be understood or used without a proper key.
Backend systems send data to the platform through APIs, often carrying attributes such as purchase status, subscription state, or loyalty tier. Although these systems operate in controlled environments, the data still travels across networks. API payloads in transit are encrypted using HPKE (Hybrid Public Key Encryption) in addition to transport level security, protecting sensitive information as it moves from the client’s systems into the platform.
Bulk ingestion through file uploads concentrates risk further, as a single file can contain large volumes of sensitive data. To protect this data during transfer, files are encrypted before upload using Pretty Good Privacy (PGP) encryption. This keeps file contents protected from the moment they leave the client’s environment until they are securely ingested and decrypted by the CleverTap platform.
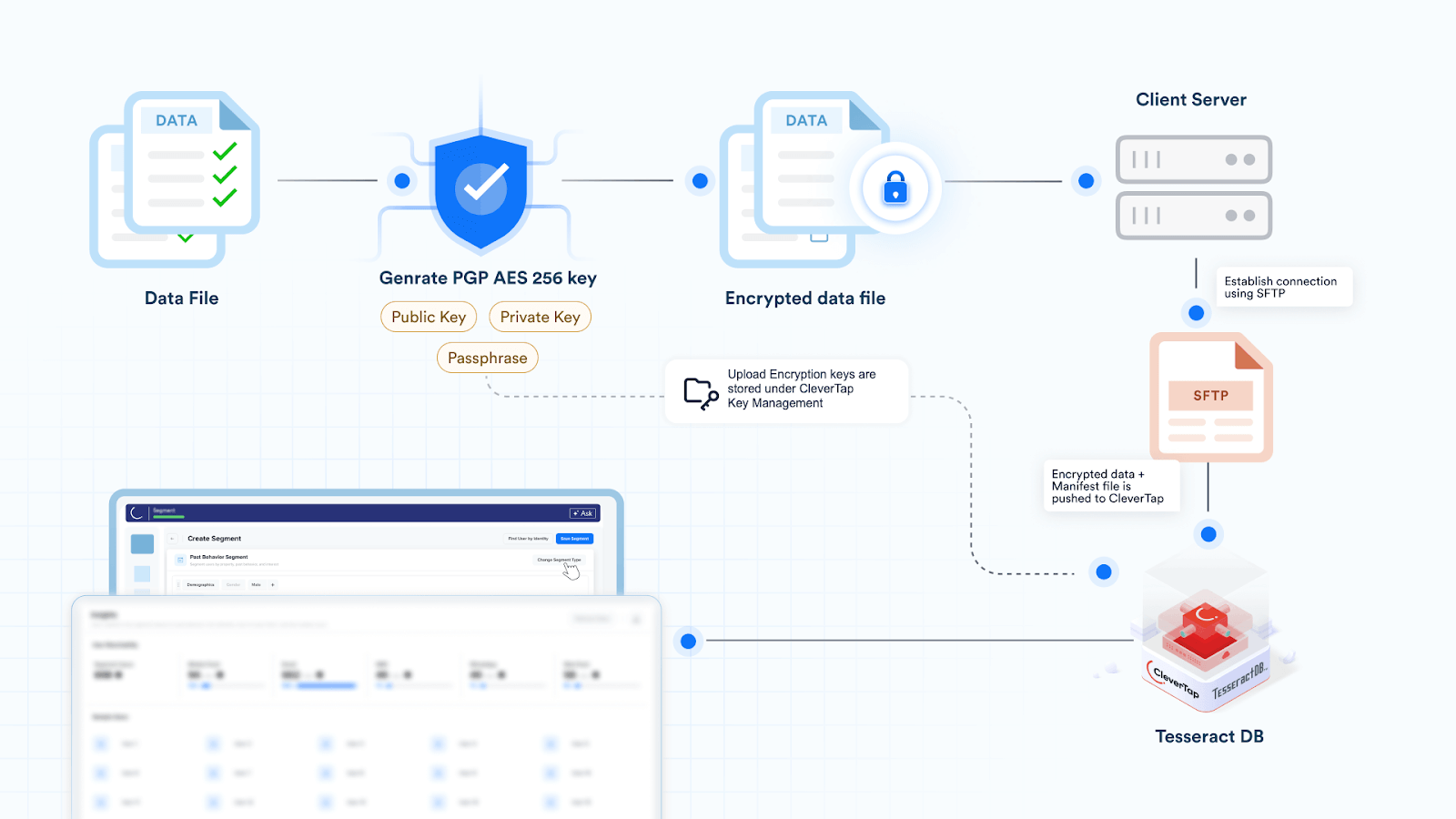
Together, these controls ensure that customer data enters the platform securely, whether it arrives in real time from devices, from backend systems, or through bulk imports.
How customer data is stored securely inside the CleverTap platform
Once customer data has entered the platform, the focus shifts to limiting exposure while the data is stored and used.
This stage includes customer profiles, event histories, and segments. These assets are accessed frequently and updated continuously, which makes them a key area of long-term risk if not protected properly.
Stored data is first protected at the infrastructure level. Data at rest is encrypted with AES 256. This reduces the impact of unauthorized access to underlying storage systems.
Protection then goes deeper for Personally Identifiable Information (PII). Field-level at-rest encryption encrypts PII independently, rather than relying only on infrastructure encryption. These values remain encrypted while stored and are decrypted only when authorized platform components need them.
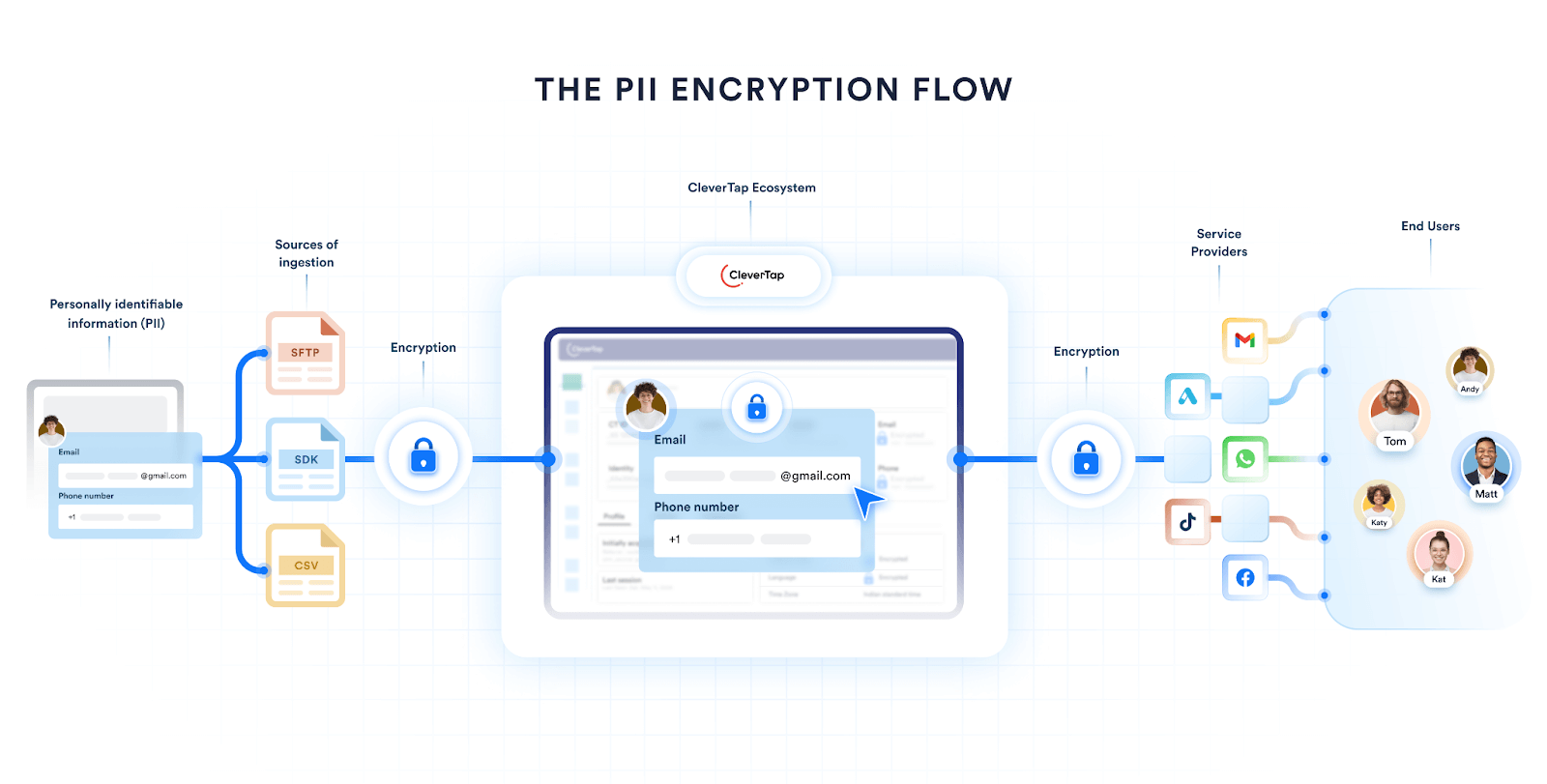
Visibility controls further reduce risk during everyday use. Not every user needs to see raw identifiers to do their job.PII masking hides sensitive fields from users who do not require direct access, allowing segmentation and analysis without exposing personal data.
At this stage, encryption keys are managed by CleverTap. Customer-managed key models and stronger governance controls apply when stricter requirements exist and are covered later as advanced protections.
How data is accessed securely inside the platform
Once data is stored, the next source of risk is how it is accessed during day to day use. This stage focuses on controlling who can enter the CleverTap platform, what they are allowed to do, and how their actions are tracked.
Customer engagement platforms typically support many users with different responsibilities. Marketers build segments and campaigns. Analysts review aggregated data and performance trends. Administrators manage configuration. In some cases, agencies or partners are also given access. Not all of these users need the same level of visibility or control.
Access protection starts with identity. Single Sign On (SSO) ties platform access to the client’s existing identity provider, keeping authentication aligned with corporate policies. Multi Factor Authentication (MFA) adds an additional verification step, reducing the risk of compromised credentials being misused.
Authorization determines what users can see and do after they log in. Advanced Role Based Access Control (RBAC) allows access to be defined by role, limiting which data, features, or actions are available to different users.
Session controls and network restrictions add further safeguards. Session timeouts reduce the risk of unattended access, especially in shared or remote environments. Domain whitelists and IP whitelists restrict where access can originate from, helping ensure that only approved environments and users can reach the platform.
Visibility into access completes this layer. Audit logs record user activity within the platform, providing a clear trail of who accessed data, what actions were taken, and when they occurred. This is critical for internal reviews, investigations, and compliance assessments.
How customer data is secured when it moves out for activation and advanced governance controls
Customer engagement platforms activate data beyond their own boundaries. Once data leaves the platform, data security controls must account for third-party networks, regional regulations, and client governance requirements.
Outbound activation commonly includes delivery through Communications Platform as a Service (CPaaS). CPaaS refers to the infrastructure that enables brands to send communications such as SMS and email through external delivery providers. Because these workflows rely on third-party networks, encryption is essential to prevent exposure outside the platform.
Customer communication data flowing through CleverTap’s CPaaS layer is encrypted using AES 256 This protects customer identifiers and message content as they move through delivery providers.
Some data also exists temporarily outside the platform. CleverTap SDKs may store limited data on user devices to support engagement workflows. Encrypting SDK data at rest on the device reduces exposure if a user’s device is compromised or accessed without authorization.
For clients with stricter governance requirements, additional controls apply at this stage.
Bring Your Own Key (BYOK) changes how encryption keys are governed. By default, encryption keys are managed by CleverTap. With BYOK, the client retains control over encryption keys, including how they are stored, rotated, and revoked. This supports internal security policies and audit requirements where key ownership is mandatory.
In some regions, encryption alone is not sufficient. Certain regulations restrict how PII data can be stored or transferred across international borders. In these environments, PII data are not permitted to leave countries at all.
This is where tokenization applies. Tokenization replaces personal or regulated data with non sensitive tokens before the data is sent to or stored in CleverTap. The original data remain within the client’s country and are compliant with local data residency regulations
Proving security posture and audit readiness
Security controls matter, but they also need to be demonstrable. For most companies, data security is validated through internal reviews, vendor risk assessments, and external audits. This is where documentation, consistency, and independent verification become important.
CleverTap maintains certifications and compliance alignments such as ISO 27001, AICPA SOC 2, General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), and Health Insurance Portability and Accountability Act (HIPAA) readiness. These frameworks validate how security controls are designed, implemented, and governed across the platform.
When combined with lifecycle based protections across ingestion, storage, access, and activation, these certifications provide a clearer and more defensible security posture. They allow teams to demonstrate not only that data is protected, but also how that protection holds up under scrutiny.
| Free Security Features | Paid Security Features |
| Single Sign On (SSO) | PII Encryption |
| Multi Factor Authentication (MFA) | Data Encryption at Rest (within CleverTap) |
| Advanced RBAC | SDK Encryption at Rest (on user device) |
| IP Whitelisting | SDK Encryption in Transit (incoming) |
| Domain Whitelisting | File upload Encryption in Transit (incoming) |
| Session Timeout | API encryption in Transit (incoming) |
| Audit Logs | CPaas Encryption in Transit (outgoing) |
| PII Masking | BYOK (Bring Your Own Key) |
| ISO 27001, AICPA SOC 2, EU GDPR, CCPA, HIPAA compliance | PII Tokenization |
Security as the foundation of customer trust
Customer engagement depends on trust. Customers share their data with the expectation that it will be handled responsibly, used appropriately, and protected consistently. When that trust is broken, the impact extends beyond compliance or financial cost. It affects brand credibility and long term relationships.
Ultimately, strong data security enables responsible customer engagement. It allows teams to personalize experiences, automate journeys, and scale communication without compromising the integrity of customer data. When security is built into how data flows through the platform, trust is not treated as a promise. It becomes a property of the system itself, sustained through consistent controls, clear governance, and deliberate design.
Sagar Hatekar 
Leads product managementExpert in Marketing Analytics & Engagement platforms.
Free Customer Engagement Guides
Join our newsletter for actionable tips and proven strategies to grow your business and engage your customers.